In this blog post we want to have an closer look into an way how you can collect data from an client system to monitor them. With endpoint analytics Microsoft provides an very powerful way to analyse clients, remediate potential issues or also detect anomalies in the field. If you are interested in unaggregated and more detailed data to build custom solutions than the log analytics management agent is the right solution for you. This is the first part of an small series with two parts. In this part we will check how this service works and how to setup und in th eother part how you can work with the data.
Content
- Content
- What is the azure monitor agent?
- How does it work?
- What are the prerequisites?
- How to deploy the monitoring agent
- Create data collection rule
- Create a Monitored Object
- Troubleshoot
- Additional resources
What is the azure monitor agent?
The Azure Monitor Agent (AMA) collects monitoring data from the operating system of an Azure or an physical machine and delivers it to an Azure Monitor Log analytics to consume it with Azure Monitor for other services, such as Microsoft Sentinel and Microsoft Defender for Cloud. You can collect performance data as well as event logs or also other telemetrie.
How does it work?
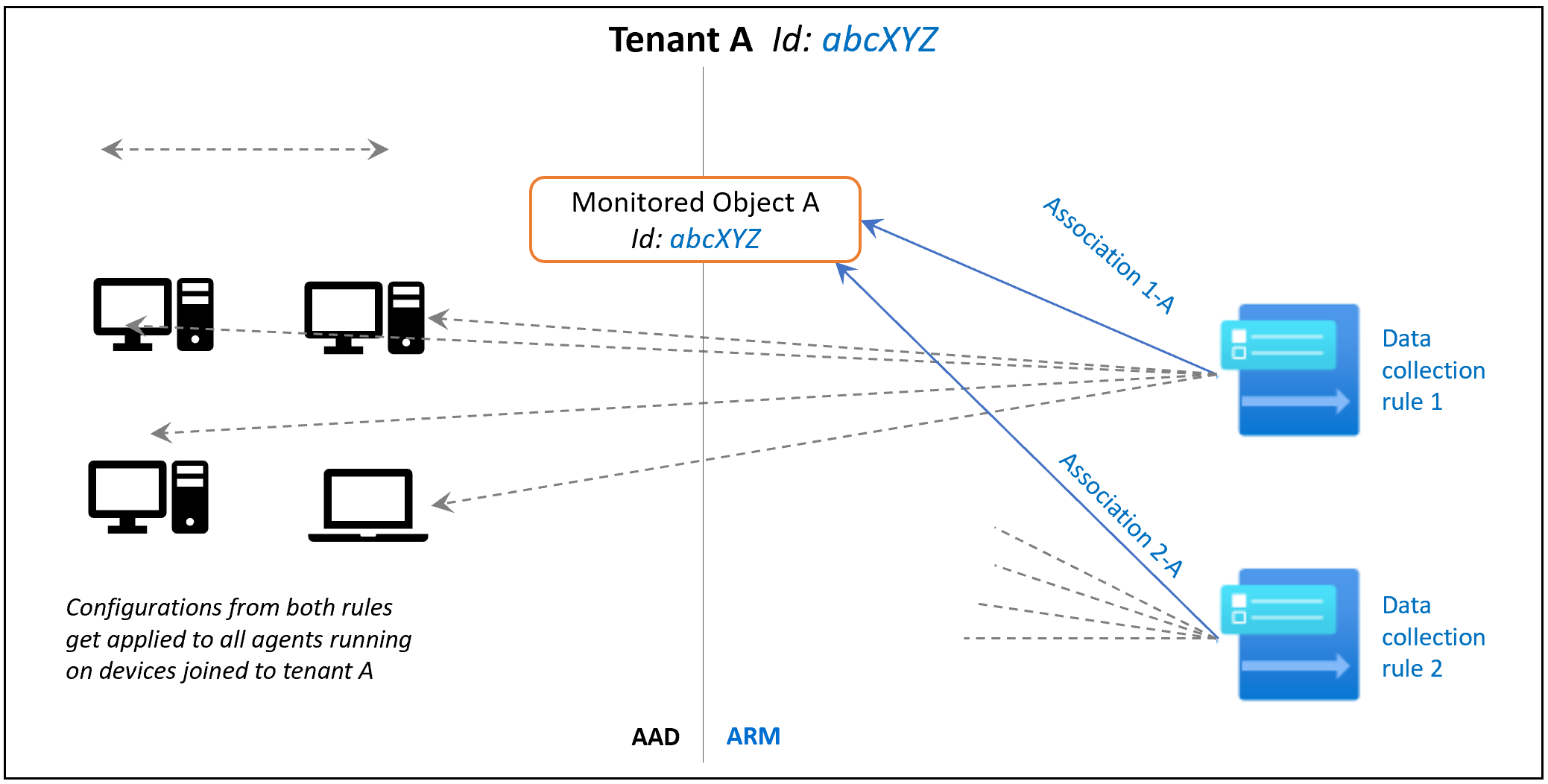
First, you required to establish a ‘Monitored Object’ (MO), which acts as a representation of the Azure AD tenant within the Azure Resource Manager (ARM). It is the ARM entity that Data Collection Rules link to. The MO only needs to be established once for any quantity of machines under a single AAD tenant. The current limitation of this connection is that it’s only applicable to the Azure AD tenant scope. This implies that any settings applied to the AAD tenant will also be applied to all devices within that tenant that run the agent installed via the client installer. This does not affect agents installed as a VM extension. The attached image illustrates this process:

Given that an MO is a tenant-level resource, the scope of the permissions will be greater than a subscription scope. Therefore, an Azure tenant administrator might be required to carry out this step. To elevate the Azure AD Tenant Admin to Azure Tenant Admin. This will provide the Azure AD admin with ‘owner’ permissions at the root scope.
What are the prerequisites?
- Network access to the following endpoints:
- * .global.handler.control.monitor.azure.com
*.handler.control.monitor.azure.com<log-analytics-workspace-id>.ods.opinsights.azure.com
- Microsoft Visual C++ Redistributable
- Windows client OS
- The machine must be domain joined to an Azure AD tenant (AADj or Hybrid AADj machines) to get an device token
- Azure Tenant admin permissions
If you are AzureAD Tenant admin you can elevate your permissions to Azure Tenant admin with this instruction or more information below.
How to deploy the monitoring agent
Create log analytics workspace
- Log in to the Azure portal
- Search for Log Analytics and select the Log Analytics workspace service

- Click + Create

- Select the Subscription and a Resource group or create a new one
- Enter an Name for the Workspace and select a Region
- Click Review + Create

- Click Create

Agent installation and deployment
- Download the MSI from the following URL
msiexec /i AzureMonitorAgentClientSetup.msi /qn
| Parameter | Description |
|---|---|
| INSTALLDIR | Directory path where the agent binaries are installed |
| DATASTOREDIR | Directory path where the agent stores its operational logs and data |
| PROXYUSE | Must be set to “true” to use proxy |
| PROXYADDRESS | Set to Proxy Address. PROXYUSE must be set to “true” to be correctly applied |
| PROXYUSEAUTH | Set to “true” if proxy requires authentication |
| PROXYUSERNAME | Set to Proxy username. PROXYUSE and PROXYUSEAUTH must be set to “true” |
| PROXYPASSWORD | Set to Proxy password. PROXYUSE and PROXYUSEAUTH must be set to “true” |
| CLOUDENV | Set to Cloud. “Azure Commercial”, “Azure China”, “Azure US Gov”, “Azure USNat”, or “Azure USSec |
- You can find more information here
- To ensure that the installation is completed open the Control panel and navigate to Control Panel\Programs\Programs and Features and check if you can find the Azure Monitor Agent

You can create a intunewin file to deploy the agent as a win32 app via Intune. You can find a instruction here.
Create data collection rule
- Open the Log analytics workspace and select Agents
- Click Data Collection Rules

- Enter an Rule name and select the Subscription / Resource group and the Region
- Click Next

- Click + Add resource
- Select the resources (If you have one in the list you want to add like a Azure VM) and click Apply
- Click Next

- Click + Add data source
- Select an type and the metrics

- Select Destination and select Azure Monitor Logs
- Select your workspace
- Click Add data source and Next

- Click Create

Create a Monitored Object
Assign the Monitored Object Contributor role
- Generate an AssignmentGUID via this link or run
[guid]::NewGuid()in powershell - Assign the Monitored Object Contributor role to an user or an group. You have to do this via the management api call:
Call
PUT https://management.azure.com/providers/microsoft.insights/providers/microsoft.authorization/roleassignments/{roleAssignmentGUID}?api-version=2021-04-01-previewBody
Fill in here the Id of your user or group
{
"properties":
{
"roleDefinitionId":"/providers/Microsoft.Authorization/roleDefinitions/56be40e24db14ccf93c37e44c597135b",
"principalId":"aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa"
}
}
Header
- Add an Azure ARM Token. You can get this token via the Get-AzAccessToken command.
Create Monitored Object
During this stage, the Monitored Object is established specifically for the Azure AD Tenant scope. Its purpose is to serve as a representation of client devices that have been authenticated with the identity of that particular Azure AD Tenant.
- Run the following command and replace the AADTenant with the Id of your tenant
Call
PUT https://management.azure.com/providers/Microsoft.Insights/monitoredObjects/{AADTenantId}?api-version=2021-09-01-previewBody
Fill in here the location
{
"properties":
{
"location":"westeurope"
}
}
Associate DCR to Monitored Object
- Run the following command and replace the MOResourceId, associationName, subscriptionId, resourceGroupName, DCRName with the correct enriex
Call
PUT https://management.azure.com/{MOResourceId}/providers/microsoft.insights/datacollectionruleassociations/{associationName}?api-version=2021-09-01-previewBody
Fill in here the location
{
"properties":
{
"dataCollectionRuleId": "/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Insights/dataCollectionRules/{DCRName}"
}
}
Script
The script is from the official ms documentation but adapted that it works and ti simplify it.
- You can run this PowerShell script to have the full workflow
$TenantID = "" #Your Tenant ID
$SubscriptionID = "" #Your Subscription ID
$ResourceGroup = "" #Your resourcegroup
$associationName = "" #You can define your custom associationname, must change the association name to a unique name, if you want to associate multiple DCR to monitored object
$DCRName = "" #Your Data collection rule name
$Location = "" #Use your own loacation westeurope
$UserPrincipalId = ""
Connect-AzAccount -Tenant $TenantID
#Select the subscription
Select-AzSubscription -SubscriptionId $SubscriptionID
#Create Auth Token
$auth = Get-AzAccessToken
$AuthenticationHeader = @{
"Content-Type" = "application/json"
"Authorization" = "Bearer " + $auth.Token
}
# Elevate access for a Global Administrator
$uri = "https://management.azure.com/providers/Microsoft.Authorization/elevateAccess?api-version=2016-07-01"
$response = Invoke-RestMethod -Method POST -Uri $uri -Headers $AuthenticationHeader
#1. Assign ‘Monitored Object Contributor’ Role to the operator
$newguid = (New-Guid).Guid
$body = @"
{
"properties": {
"roleDefinitionId":"/providers/Microsoft.Authorization/roleDefinitions/56be40e24db14ccf93c37e44c597135b",
"principalId": `"$UserPrincipalId`"
}
}
"@
$requestURL = "https://management.azure.com/providers/microsoft.insights/providers/microsoft.authorization/roleassignments/$newguid`?api-version=2021-04-01-preview"
Invoke-RestMethod -Uri $requestURL -Headers $AuthenticationHeader -Method PUT -Body $body
##########################
#2. Create Monitored Object
# "location" property value under the "body" section should be the Azure region where the MO object would be stored. It should be the "same region" where you created the Data Collection Rule. This is the location of the region from where agent communications would happen.
$requestURL = "https://management.azure.com/providers/Microsoft.Insights/monitoredObjects/$TenantID`?api-version=2021-09-01-preview"
$body = @"
{
"properties":{
"location":`"$Location`"
}
}
"@
$Respond = Invoke-RestMethod -Uri $requestURL -Headers $AuthenticationHeader -Method PUT -Body $body -Verbose
$RespondID = $Respond.id
##########################
#3. Associate DCR to Monitored Object
#See reference documentation https://learn.microsoft.com/en-us/rest/api/monitor/data-collection-rule-associations/create?tabs=HTTP
$requestURL = "https://management.azure.com$RespondId/providers/microsoft.insights/datacollectionruleassociations/$associationName`?api-version=2021-09-01-preview"
$body = @"
{
"properties": {
"dataCollectionRuleId": "/subscriptions/$SubscriptionID/resourceGroups/$ResourceGroup/providers/Microsoft.Insights/dataCollectionRules/$DCRName"
}
}
"@
Invoke-RestMethod -Uri $requestURL -Headers $AuthenticationHeader -Method PUT -Body $body
#(Optional example). Associate another DCR to Monitored Object
#See reference documentation https://learn.microsoft.com/en-us/rest/api/monitor/data-collection-rule-associations/create?tabs=HTTP
$requestURL = "https://management.azure.com$RespondId/providers/microsoft.insights/datacollectionruleassociations/$associationName`?api-version=2021-09-01-preview"
$body = @"
{
"properties": {
"dataCollectionRuleId": "/subscriptions/$SubscriptionID/resourceGroups/$ResourceGroup/providers/Microsoft.Insights/dataCollectionRules/$DCRName"
}
}
"@
Invoke-RestMethod -Uri $requestURL -Headers $AuthenticationHeader -Method PUT -Body $body
#4. (Optional) Get all the associatation.
$requestURL = "https://management.azure.com$RespondId/providers/microsoft.insights/datacollectionruleassociations?api-version=2021-09-01-preview"
(Invoke-RestMethod -Uri $requestURL -Headers $AuthenticationHeader -Method get).valueDon’t forget to remove also the elevated access. It is explained here.
Troubleshoot
- You can find an log connector under Program Files \Azure Monitor Agent
- When you execute the CollectAMALogs.ps1 than an Folder at the Desktop with logs will be generated


[…] Azure Monitor Agent to monitor Windows devices (1/2) – Setup […]
LikeLike